Questions on Server-side Code
Some are asking about our servers

The HydraVeil client is open source, with a copyleft GNUv3 license. But some ask,
Q: Is HydraVeil’s server-side code also open source?
A: The answer is that the server-side billing code is unrelated to HydraVeil itself. Because:
Any Config Files
The app draws upon the WireGuard or proxy configs in the profiles folder. ANY wireguard configuration or ANY socks5 proxy can be inserted into those folders. Specifically the folder is:
.config/hydra-veil/profiles
For example this is a proxy.json going to Iceland, which can be modified to connect to ANY proxy. There is no vendor lock-in. This is copyleft open source.
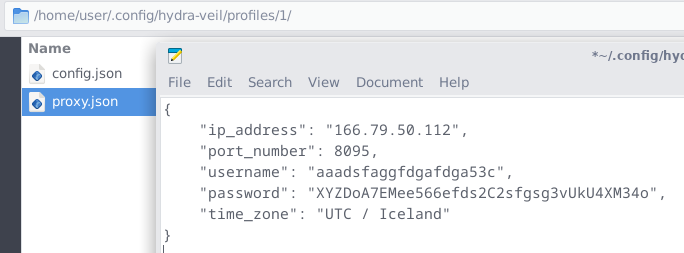
Note: Please note the ports for the proxy JSON connection are different than the ports used for the browser itself (which is internal due to the isolated environment).
Any Browser Apps
And any browser can be used if it’s in that folder with the right ports. The ports are 58287 for Wireguard, and 48977 for socks5. To view this go to “about:policies” which show the enterprise resource policies.
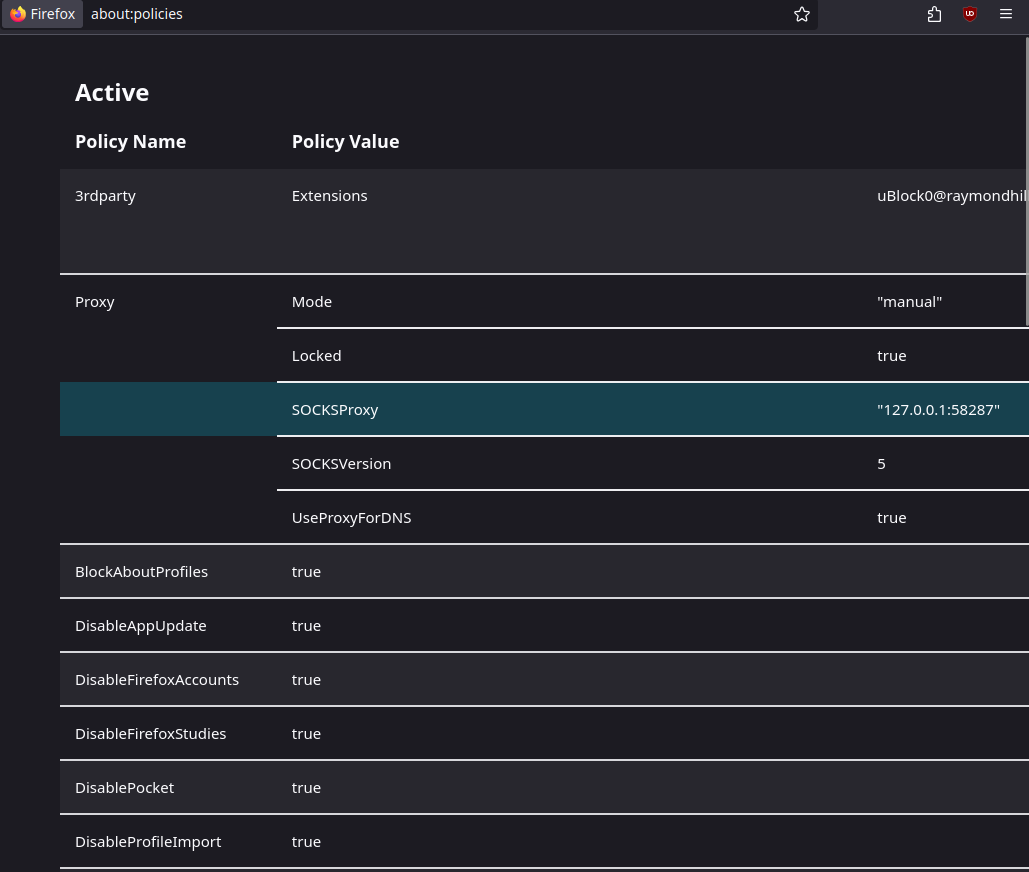
Please get a better understanding of our technology from our “Behind the Tech” articles.
You can self-host
Therefore, you can self-host Wireguard or socks5 proxies for use with HydraVeil right now. Or you can insert negligent Mullvad, with their centralized international server providers and Gmail-controlled Wireguard configs right in there.
No Forced Connection to Us
HydraVeil does NOT connect to Simplified Privacy on startup or use. Our server-side code is just billing, serving browsers, and then you connect to your choice of the WG or proxy node directly. Only if you OPTIONALLY choose to “sync” does it then connect to our billing server for new plans/data.
Can’t verify anyway
And even if we opened up the code of our exact configs on the WG nodes or Socks5 proxy servers, the end-user can’t verify we aren’t logging server-side. This is why the use of a 2nd layer “browser-only” VPN is so important, to hide your identity with the system-wide layer-1. So your skepticism represents the critical need for HydraVeil to begin with.

Mullvad doesn’t
Negligent Mullvad doesn’t open up their billing server. They only open source the browser the CIA-funded-Tor literally made for them. Which Trump is cutting some of the budget for, so I’m not expecting much future innovation from Mullvad. I hope in the future, they can figure out how to even package Tor Browser themselves, without the CIA’s help.
Therefore,
Given complete freedom under GNU, with no vendor lock-in, it’s irrelevant that we have not yet opened up our WG nodes. And even better, this will be done in the future, after further decentralization of our network.
The only reason someone would want to press us further on open sourcing a billing server, is to literally copy the entire business model. And if we fail, it only would represent that open source itself is a dead-end career… and so in the future, only the government will fund FOSS. Because they’re even better than me at losing money.
Further Questions?
If you have other questions, please contact support.
If you really want to learn and take your privacy to the next level, subscribe to our new content via: Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts

Even without Linux, Why use our VPN?
What's the Difference?
[SP]
May 21, 2025

Windows VPN Tutorial
Easy and Fast Tutorial for Windows Users.
[SP]
May 21, 2025

iPhone (or iPad) VPN Tutorial
Easy and Fast Tutorial for Apple iPhone Users.
[SP]
May 18, 2025

Mac VPN Tutorial
Easy and Fast Tutorial for Apple Users.
[SP]
May 18, 2025